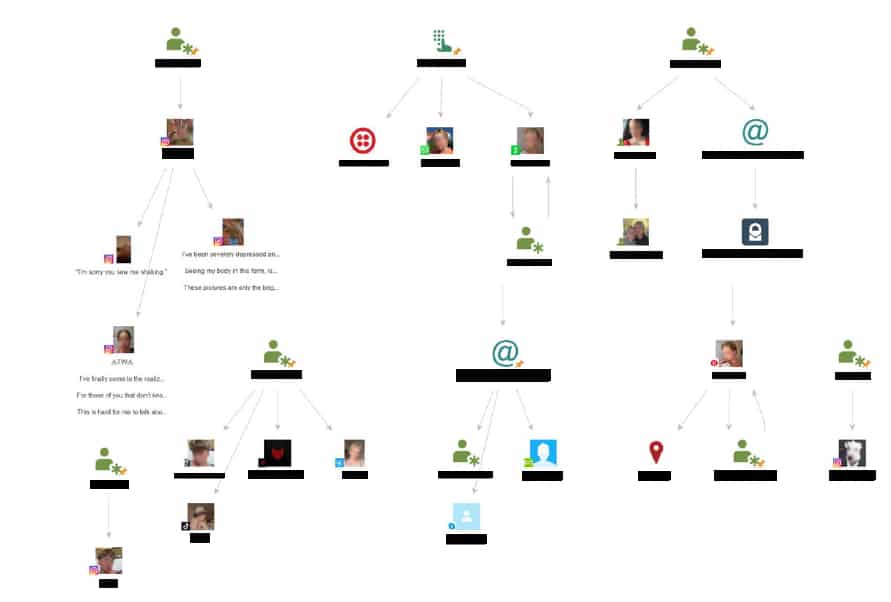
Social Media Discovery: Visualizing an Individual’s Online Footprint
November 30, 2022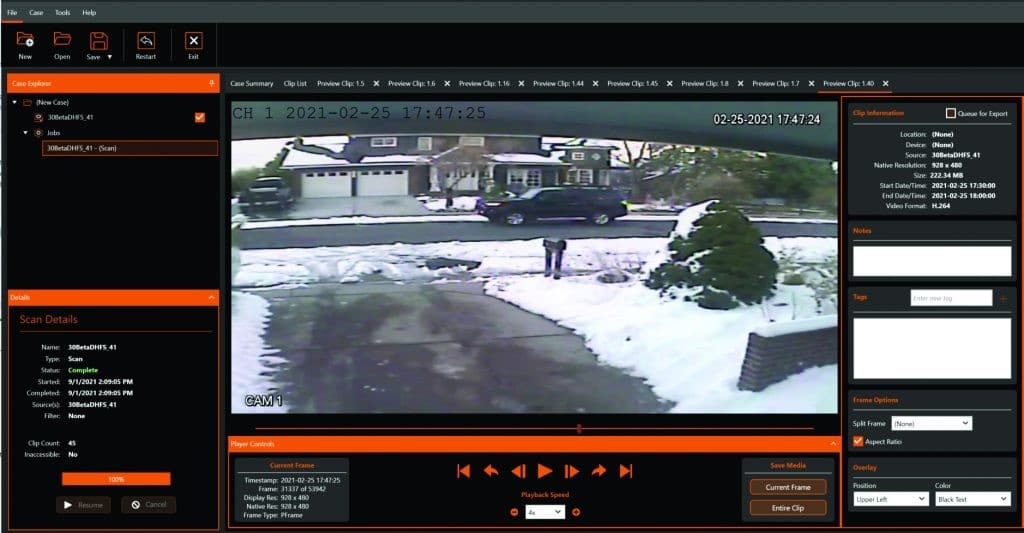
DVR Examination and Recovery in Digital Forensics
January 24, 2023Written by: Jade Thuo
Recently we have seen a spike in sales for the DSTIKE watch and although some may be using it for legitimate research purposes, we fear that many are using it in criminal actions.

The DSTIKE Watch is a small, portable device that is designed to disrupt and disable Wi-Fi networks. It is often used by cybersecurity professionals and researchers to test the security of Wi-Fi networks and identify vulnerabilities.
One of the primary uses of the DSTIKE Watch is to conduct a “denial of service” (DoS) attack on a Wi-Fi network. This type of attack involves flooding the network with traffic, disrupting its normal functioning and rendering it inaccessible to users. The DSTIKE Watch is able to achieve this by rapidly sending data packets to the target network, overwhelming its capabilities and causing it to crash.
While the DSTIKE Watch can be a useful tool for testing the security of Wi-Fi networks and identifying vulnerabilities, it can also be misused for malicious purposes. For example, an attacker could use the DSTIKE Watch to disrupt a public Wi-Fi network, preventing legitimate users from accessing the internet. Therefore, it is important to use the DSTIKE Watch responsibly and only for lawful purposes.
In addition to its ability to conduct DoS attacks, the DSTIKE Watch also includes a number of other features that can be useful for cybersecurity professionals. These include the ability to scan for nearby Wi-Fi networks and identify their characteristics, such as their security protocols and signal strength. It can also be used to capture Wi-Fi traffic and analyze it for signs of malicious activity.
Overall, the DSTIKE Watch is a powerful tool that can be used for both good and bad purposes. While it can be useful for identifying vulnerabilities in Wi-Fi networks and improving their security, it is important to use it responsibly and only for lawful purposes.
Hardware is readily available on Amazon.
With multiple devices using the DSTIKE firmware and Hardware components one can simply browser Amazon and find the necessary parts to build the watch for around 25 USD to 75 USD.
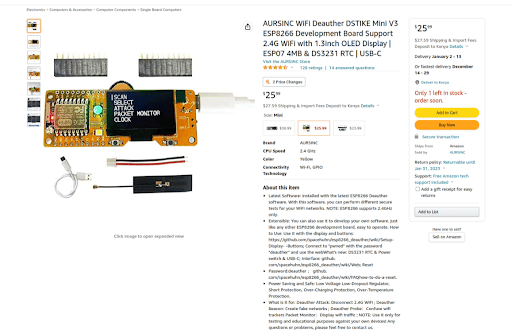
The DSTIKE watch features are below:
- Latest Software: installed with the latest ESP8266 Deauther software. With this software, you can perform different secure tests for your Wi-Fi networks. NOTE: ESP8266 supports 2.4GHz only.
- Extensible: You can also use it to develop your own software. just like any other ESP8266 development board, easy to operate. How to Use: Use it with the display and buttons: https://github.com/spacehuhn/esp8266_deauther/wiki/Setup-Display- -Buttons; Connect to “pwned” with the password “deauther” and use the webWhat’s new: DS3231 RTC & Power switch & USB-C; Interface: github.com/spacehuhn/esp8266_deauther/wiki/Web; Reset
- Password:deauther ; github.com/spacehuhn/esp8266_deauther/wiki/FAQhow-to-do-a-reset.
- Power Saving and Safe: Low Voltage Low-Dropout Regulator, Short Protection, Over-Charging Protection, Over-Temperature Protection.
- What is it for Deauther Attack: Disconnect 2.4G Wi-Fi ; Deauther Beacon: Create fake networks; Deauther Probe: Confuse Wi-Fi trackers Packet Monitor: Display Wi-Fi traffic; NOTE: Use it only for testing and educational purposes against your own devices! Any questions or problems, please feel free to contact us.
How does a Deauth Attack Work?
A Wi-Fi de-authentication attack is a type of denial-of-service attack that targets communication between a user and a Wi-Fi Access Point. This attack disrupts the communication between the devices causing them to be offline. This will disrupt widely used devices such as Ring Doorbell cameras.
We tested this device and found that from more than 40 feet away we can disrupt a Ring doorbell camera.
Be careful as you see those wearing these devices as they can be very disruptive. If your Ring doorbell or Wi-Fi stops working and someone is at your door, take extra precautions.

